Badblood by Secframe
Fills a Microsoft Active Directory Domain with an OU structure and thousands of objects.
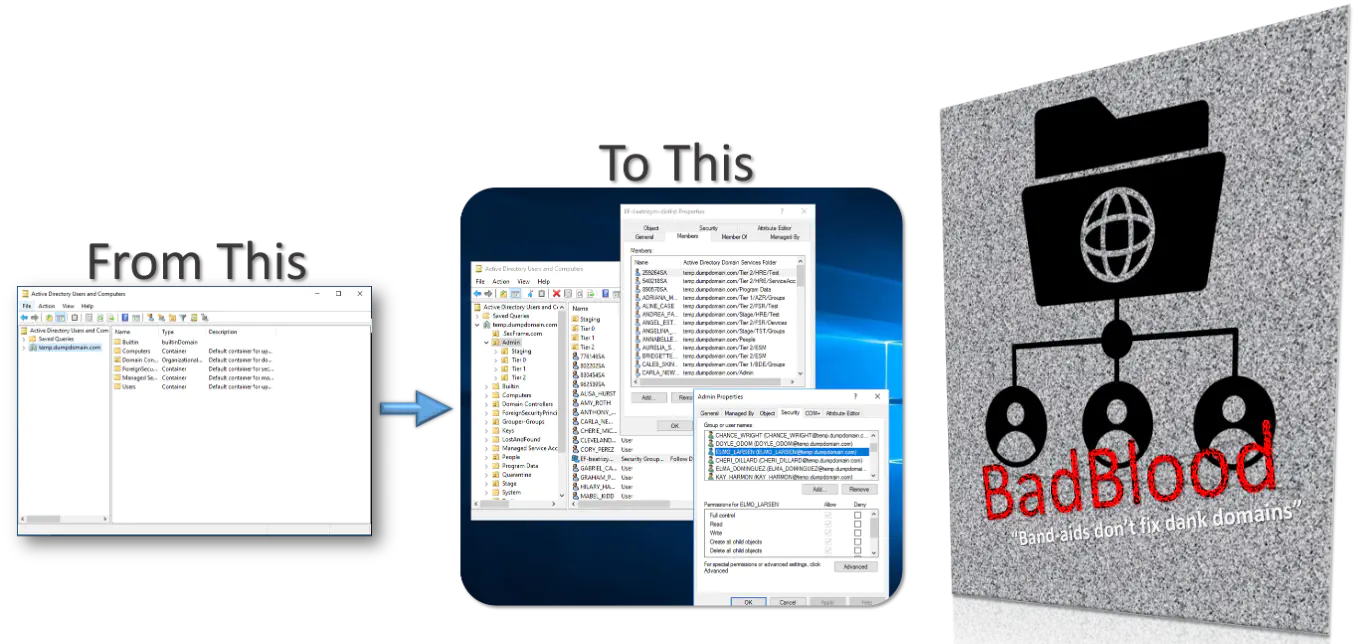
The output of BadBlood is a domain similar to one found in the real world.
Use it to:
- Start a journey into privileged identity threat hunting.
- Build a test domain
- Test vendor software